Bitdefender: “Exchange architecture reason for security problems”
Microsoft Exchange customers are still under massive pressure in 2023. After numerous successful attacks on the mail and collaboration servers in recent years, media criticize Exchange as “not repairable” – the flaw is already in the architecture. The manufacturer itself seems overwhelmed – time to switch to the secure open source alternative grommunio.
The last few years have been full of scary stories about the serious vulnerabilities with names like ProxyLogon, ProxyShell, ProxyNotShell or the PR-GAU around Microsoft’s failed ProxyNotShell-“emergency fix“ OWASSRF. All of these vulnerabilities have a few things in common: First, of course, they combine the potential for a complete loss of all data or for intrusions with ransomware. On the other hand, all these loopholes exploit a systematic vulnerability in the Exchange system architecture.
Complexity and Legacy: “Exchange is the Ideal target”
The Romanian antivirus software manufacturer Bitdefender writes that the error lies in the system. Exchange is the ideal target for attackers for various reasons – for example, because it is forced to be compatible with outdated, insecure technology (“backwards compatibility”).
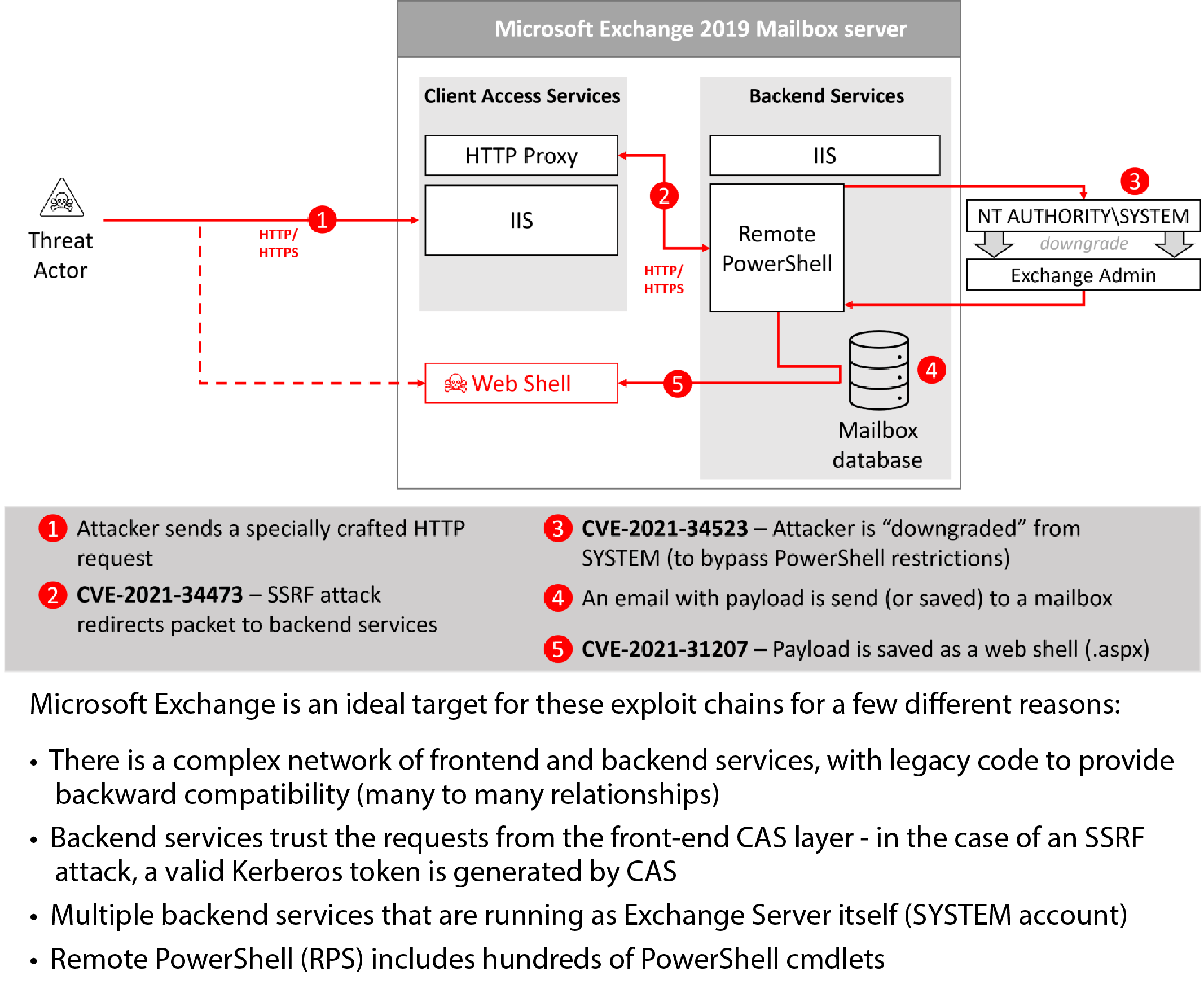
But the “complex architecture of front-end and back-end services” with vast amounts of obsolete legacy code also opens the door to attackers. According to Bitdefender, if backend services run with the privileges of the Exchange Server itself, they are vulnerable via the frontends – which all the “PROXY” vulnerabilities mentioned knew how to exploit.
Complex architecture with legacy connection
In these attack vectors, hackers use vulnerabilities in the frontends as a proxy, so to speak, to access the backend servers with the valid authentication of the frontend services. These allow access (thanks to valid Kerberos certificates) to additional services, such as a Powershell with administrator rights – and thus comprehensive access to the corporate network.
Bitdefender warns: With the architecture operated by Microsoft, there is neither improvement in sight nor are the associated named attack variants completely named or even known. Much worse, this scenario is just one of many that lay dormant in the outdated systems based on legacy code and applications.
In a recent warning, the manufacturer Microsoft states that attackers are increasingly targeting unpatched systems, of which there are still far too many. Often, users cannot apply every patch because the software landscape does not always allow it easily. According to the IT security portal Hackernews, Microsoft itself describes its own instructions for remedial action (mitigations) as only “temporary”: only installing the recommended patches helps to ensure the security of the servers. Will this strengthen the trust lost by the customer?
Remedy: Exchange your Exchange
grommunio also has a complex architecture, but on the one hand it is transparent, implemented in secure and proven current open source technologies, developed with modern methods, tested and validated. grommunio is based on secure protocols, which are thus also used on millions of servers in the most critical security areas.
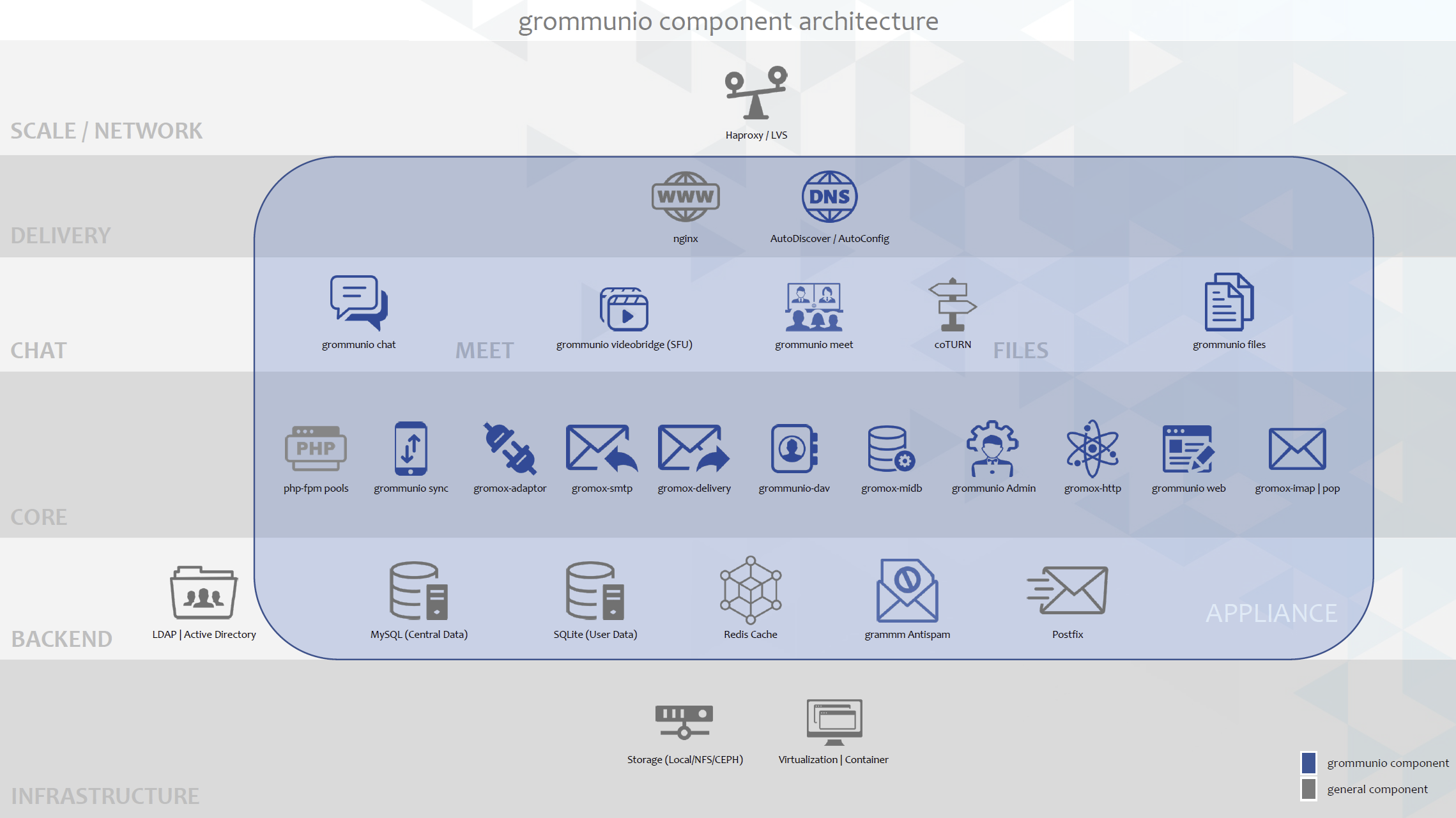
The numerous APIs of the Exchange stack used by grommunio are specified as Open Standards, completely re-implemented by the grommunio development team and constantly kept up-to-date.
In the process, grommunio has also proven itself in use in large environments, for example in “OpenSource Collaboration” on the Open Telekom Cloud.
Get an idea yourself – by looking at the source code or testing grommunio.

